Editor’s note: Quotes and information from the nonprofit C4ADS are attributed to the organization and not an individual due to privacy concerns.
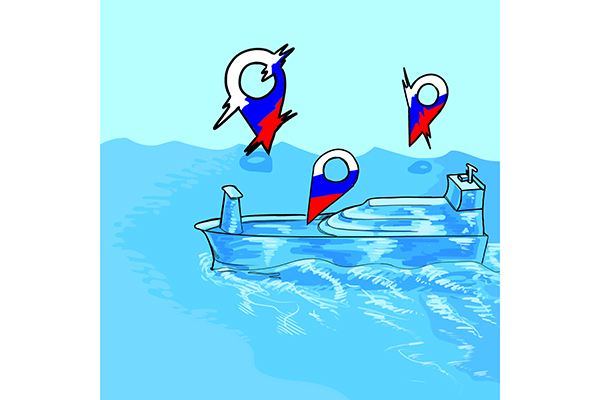
UT researchers, in association with the nonprofit C4ADS, the Center for Advanced Defense Studies, investigated reports of irregular GPS signals surrounding Russian waters and attributed them to the Russian government.
The year-long study, titled “Above Us Only Stars: Exposing GPS Spoofing in Russia and Syria,” cataloged data from ships’ automatic identification system and GPS signal data from the International Space Station and was published March 26.
Software written by Todd Humphreys, an associate professor of aerospace engineering and engineering mechanics, and his students was installed on a GPS receiver on the ISS in February 2017. On May 24, 2018, the same receiver collected anomalous GPS signals in the eastern Mediterranean Sea.
C4ADS attributed these false signals to spoofing devices used by Russia.
“(Spoofing devices) transmit a signal that the receiver thinks is a valid series of GPS signals, but the information contained in the signals does not allow the receivers to calculate a position,” said Dana Goward, president of Resilient Navigation and Timing Foundation, which helped with the study. “Receivers will give every indication that they’re functioning properly but will not be able to tell you where you are.”
C4ADS speculated how the GPS spoofing technology is employed by characterizing the signals.
“We looked at how GPS spoofing is being used to protect domestic interests within Russia and some of its occupied territories,” C4ADS said. “And that is mainly for VIP protection as well as strategic facility protection.”
Spoofing technology has likely been present in Russia for more than a decade, Humphreys said. Russia appears to have employed this technology in response to emerging drone technology.
“Russia’s defensive use of the system likely reflects genuine concern that unmanned aerial vehicle technology is well within grasp of sophisticated groups who might use (unmanned aerial vehicles) to carry out attacks against Putin or the Russian government,” said James Pope, professor in UT’s LBJ School of Public Affairs.
According to C4ADS, Humphreys and his students were able to reproduce the GPS spoofing technology for around $1000 in 2013, but the technology has become increasingly cheaper to produce since then.
“Hackers and folks in information security have been able to replicate (spoofing) capability for less than $350 and using all publicly available code,” C4ADS said.
The increasingly low cost of this technology has made spoofing accessible to nongovernmental groups, Humphreys said.
“Low cost does make it easier for independent actors, who might have either good or bad intentions, to counterfeit GPS signals,” Humphreys said. “Such spoofing is a threat to commercial aviation, to maritime traffic, to timing used by financial services and many other aspects of the modern economy.”
There are already reports of drug cartels along the U.S.-Mexican border using the technology to spoof drones used by the U.S. Customs and Border Protection agency. For now, the risk to normal day-to-day life does not seem imminent, Humphreys said.
“My view is that a spoofing of jamming attack is not likely to be catastrophic, so perhaps it’s not unreasonable to wait for such an attack before we do any sort of drastic overhaul,” Humphreys said. “GPS receivers are getting smarter and more spoof-hardened, and the sheer number of (GPS) satellites available to today’s receivers makes a spoofer job much harder.”