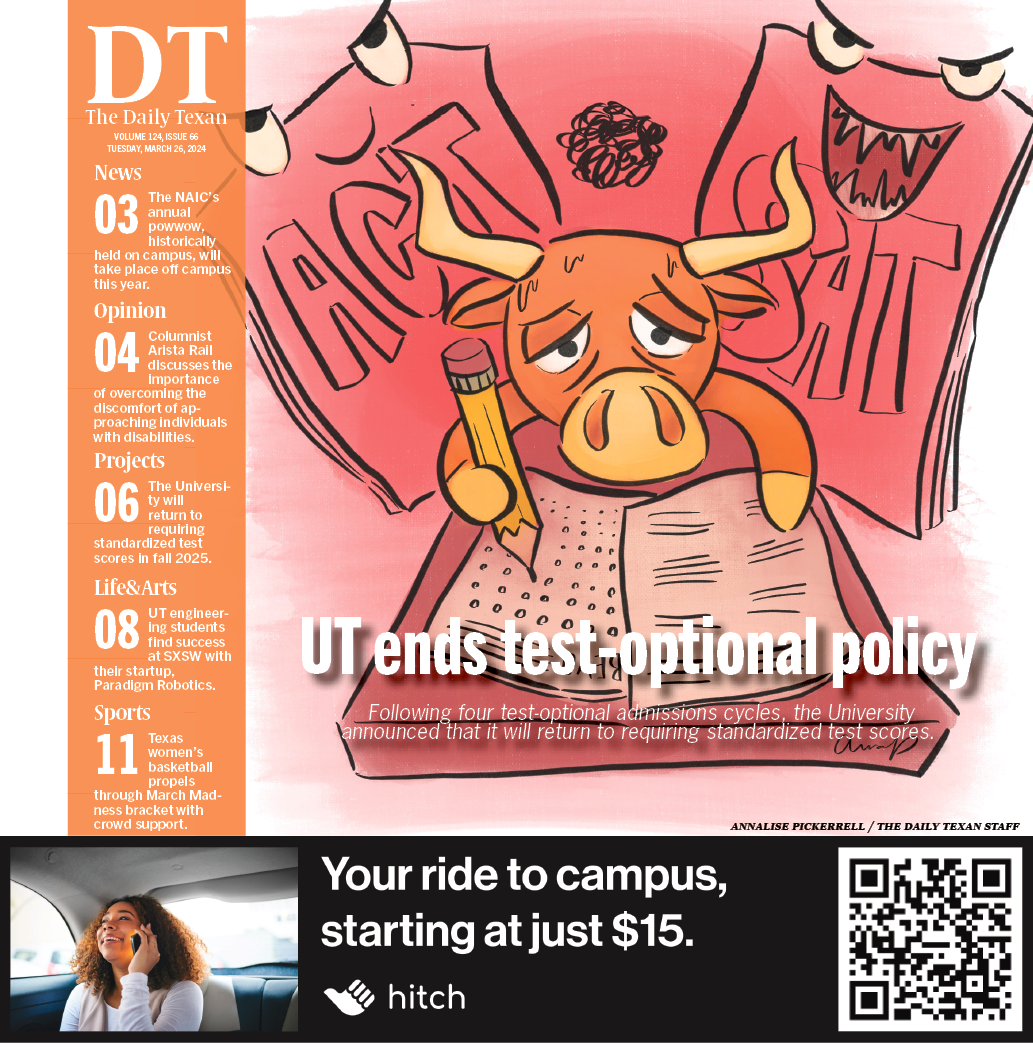
Similar to Iago’s betrayal of Othello, various components of computer operating systems can manipulate the applications and technologies we use in our computers.
Hovav Shacham, assistant professor of computer science and engineering at the University of California at San Diego, addressed UT students and faculty Monday on computer “IAGO attacks” as part of the annual computer safety series. The lecture, hosted by the Center for Information Assurance and Security, was given by Shacham because he is one of the world’s most prominent researchers in his field, said center director Vitaly Shmatikov.
“His results are very new and have yet to be published, but they have serious implications for a lot of ongoing research on secure systems,” Shmatikov said.
A sequence within a computer system can lead a supposedly protected process to act against its original interests and force the hardware-software interface, or kernel, to do whatever it wants, Shacham said at the lecture. If the kernel is untrusted, even a reliable application could be misused, he said.
“Designing and implementing secure systems is very difficult and a lot of thought goes into understanding the risks,” Shmatikov said about Shacham’s work. “It is necessary to have people like Shacham carefully investigating the true level of security provided by modern computer systems.”
Shacham said his work revolves around implementing a new supervisor within the bridge between application use and actual data usage to prevent components of operating systems from manipulating the true purpose of our computer use.
Shacham said these “IAGO attacks” occur when the kernel, which is responsible for managing the communication between the hardware and software components of the system, successfully subverts the application from its original goal. The kernel attempts to make it do anything it wants to, so if the kernel is untrusted, all the data could be lost or influenced in an unintended way, he said.
“Operating system tasks are performed differently with different kernels, so each situation is different,” Shacham said.
“However, the supervisor has to be applied in order to separate the application and the kernel.”
“This separation would prevent the kernel from abusing its power over the application,” Shacham said.
Computer science graduate student Deepak Goel said listening to Shacham is not only interesting, but its relevance to the average computer user is also important.
“Even if we think some of our actions on the computer are trivial, it is necessary for it to all be safe and his work is making that possible,” Goel said.
Printed on Tuesday, March 6, 2012 as: Lectureer speaks on secure systems